
Stop Salesforce Attacks
Arovy is the only solution that blocks unauthorized Salesforce connected apps. With the rise of bad actors (e.g. ShinyHunters, UNC6040, Salesloft Drift) targeting Salesforce customers, now is the time to lock down this risk surface.
-3.png)
Trusted by 250+ leading Salesforce customers
Salesforce has Unique Security Challenges
Relying on reactive security controls isn’t enough anymore. You need a dedicated, proactive security solution, tailored for Salesforce. Arovy is purpose-built to address the unique risks with Salesforce environments.

Block Unauthorized Applications
-

Block
Arovy can automatically block new applications without disrupting your business.
-

Alert
Any new connected app that suddenly appears, or an existing app requesting expanded scopes, is detected and triggers an alert.

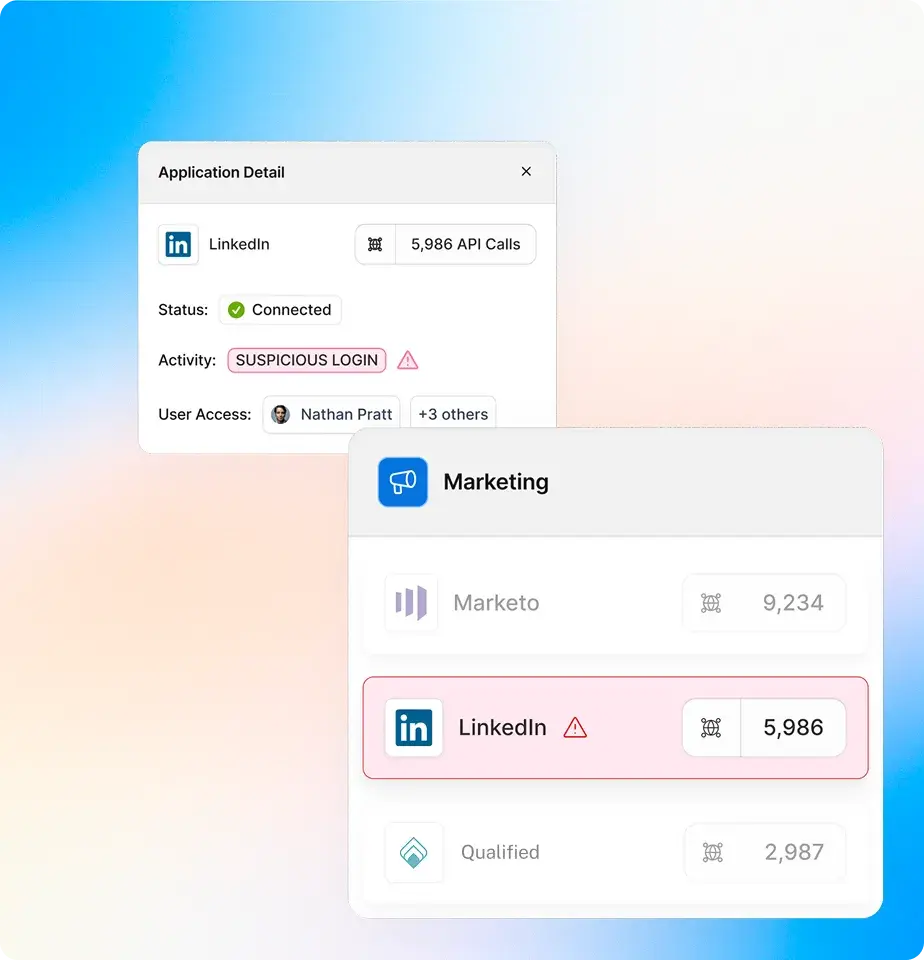
Monitor User Authentications
-
Monitor
Unexpected user authentications, especially OAuth logins from non-standard IP addresses, will generate real-time alerts.


Event Monitoring
-

Salesforce Shield Events
Arovy ingests Salesforce Shield events and spots irregular data-exfiltration patterns (e.g., hundreds of records being mass-exported by a Data Loader instance).
-

Identify
Correlating these anomalies with the connected-app alerts provide a clear signal that an active data theft is underway.

What are the UNC6040 & ShinyHunters Attacks?
A sophisticated hacking group known as UNC6040 targeted Salesforce customers in a highly coordinated phishing campaign—specifically vishing (voice phishing). Learn more here.
How would Arovy have prevented this attack?
Any new connected app that suddenly appears, or an existing app requesting expanded scopes, is detected and triggers an alert. Arovy can also automatically block unapproved applications.
In this case, the malicious Data Loader would have been flagged the moment it tried to register as a connected app.
2. New User Monitor
Unexpected user authentications, especially OAuth logins from non-standard IP addresses, generate real-time alerts.
3. Event Monitoring
Since Arovy ingests Salesforce Shield events, it would spot irregular data-exfiltration patterns (e.g., hundreds of records being mass-exported by a Data Loader instance).
Correlating these anomalies with the connected-app alerts would provide a clear signal that an active data theft was underway.
How can my organization avoid Salesforce phishing attacks?

Stop Salesforce Attacks Today
See how Arovy would have stopped this type of attack:


.webp)







.webp)



-2.webp)



-3.png?width=1000&height=667&name=Untitled%20design%20(2)-3.png)
