
Your Salesforce Data Dictionary is Dead in Excel
In most companies with Salesforce, there comes a time when someone asks: “Wait, why haven’t we been...
Product Features
Data Dictionary
Break down data silos to support governance.

Impact Analysis and Dependency Mapping
Seamless visibility into all references across your organization.
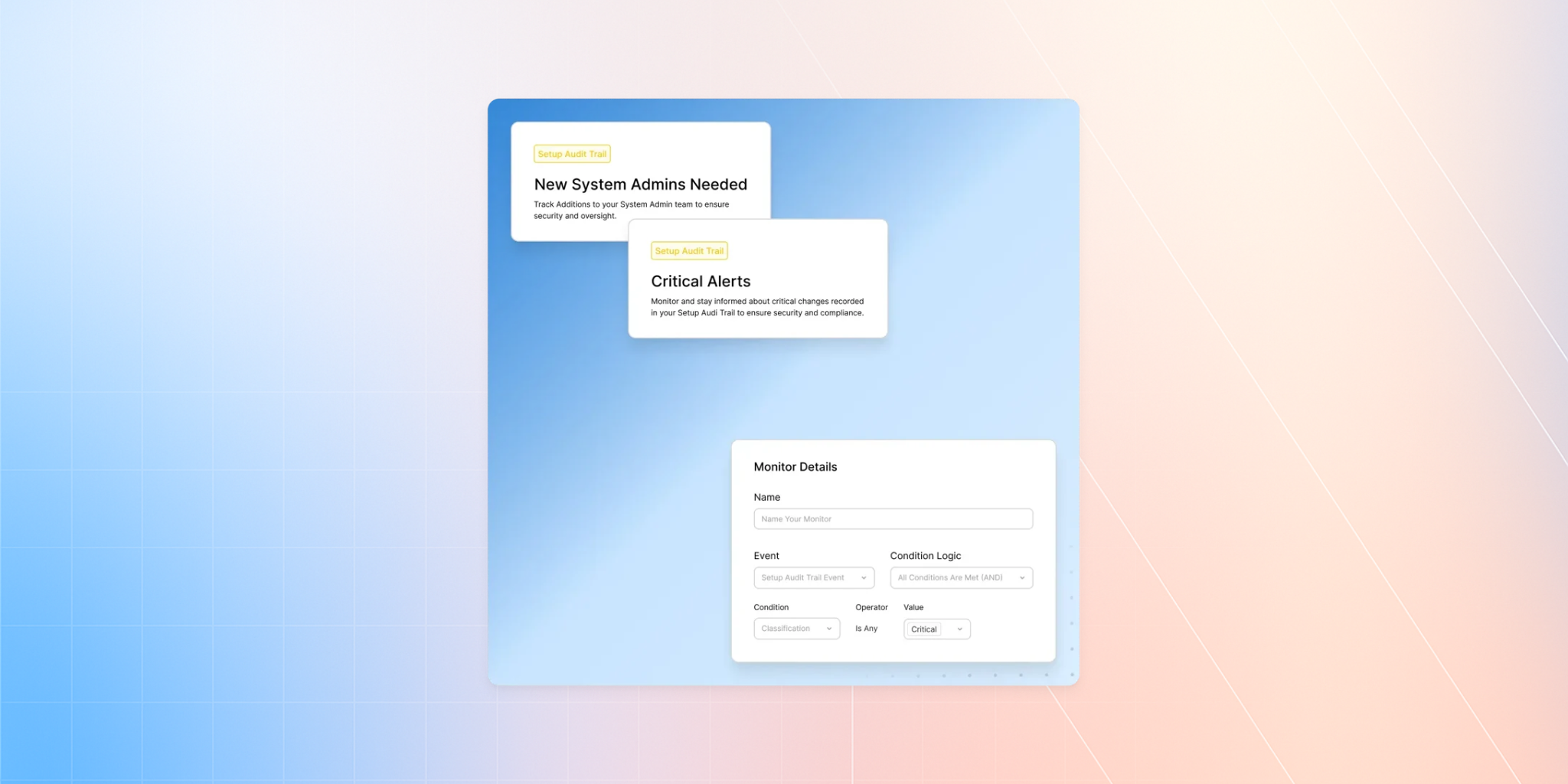
Change Tracking & Enhanced Audit Trail
Use a timeline view to track changes made across teams.
Data Classification
Ensure compliance with capture for every field added.
Application Security Monitoring
Keep a pulse on every integration and user.
API Monitoring & System Uptime
Seamlessly detect every integration outage.
Threat Detection & Risk Mitigation
Visual threat-detection and suggested action plans.
We Help You
Scope Salesforce Projects Confidently
Understand impacts across Salesforce and your integrated tech stack.
Eliminate Tech Debt with AI
Insights into every piece of data and configuration.
Monitor Setup Audit Trail
Automated access audits with Arovy.
Reduce Agentforce Risk with AI
Ensure the accuracy and usefulness of AI models.
Automate User Profile Management
Protect data and stay compliant with user access policies.
Optimize Shield Implementation
Visualize Salesforce activity to spot anomalies and prevent leaks.
Visualize Connected Apps
Get real-time visibility into apps accessing your Salesforce data.
Stop Salesforce Phishing Attacks
Block unauthorized Salesforce integrations without disrupting your business.
Latest Resources

Webinar Recording | Salesforce Data Dictionary Shortcuts
Most Salesforce teams know they need a data dictionary, yet very few successfully deploy one. We’ll break down the three proven “shortcuts” used by best-in-class Salesforce organizations.
.webp)
What an AI-Ready Salesforce Org Really Looks Like (and How to Get There)
Learn what an AI-ready Salesforce org really looks like and how to get there with a practical roadmap for org health, data dictionaries and AI governance
More From Arovy
Company Page
Learn about Arovy.
Security/Compliance
A foundation of trust for every customer.

Community
Join the WizOps Community.
Recent Resources

Sonar is now Arovy! New Name. Bigger Mission. Same Commitment.
Sonar is now Arovy. We've expanded our mission, helping Salesforce teams govern data, cut tech debt & reduce risk — while keeping the same trusted commitment.

The Power of a Data Dictionary in the Agentforce Era
Discover why a real-time data dictionary is essential for Salesforce teams in the Agentforce era. Prevent AI risks, ensure compliance, and optimize data governance.
Read up on best practices, thought leadership, and more.

In most companies with Salesforce, there comes a time when someone asks: “Wait, why haven’t we been...

Sonar is now Arovy. We've expanded our mission, helping Salesforce teams govern data, cut tech debt...

Discover how Upstack and Meritain Health use Arovy’s Salesforce Data Dictionary to prepare for AI,...

Instead of digging through CSVs, Arovy allows you to automatically ingest Setup Audit Trail entries...

Sonar is now Arovy. We've expanded our mission, helping Salesforce teams govern data, cut tech debt...

Explore key takeaways from our webinar on how Salesforce Shield Event Monitoring and connected app...
Discover Arovy’s newest features!

Secure your Salesforce APIs with strong authentication, real-time monitoring, and least privilege...

Discover why a real-time data dictionary is essential for Salesforce teams in the Agentforce era....

Salesforce access audits are essential for security and compliance. Learn how to identify risks,...
